What Is A 51% Attack

This blog post will cover:
- 51% attacks in crypto history
In this article we’ll tell you about a 51% attack and its danger for crypto. One of the most important things in the cryptocurrency world is decentralization. In common understanding, decentralization is the process of distributing and dissipating power from a central body to ordinary and independent people. Decentralization implies a shift in decision making from a single center to peripheral areas. Decentralization of cryptocurrency is the dispersal of its main resources (data) around the world, with multiple duplications to prevent their loss. The data chain (blockchain) is not stored on some main server but is located simultaneously on many computers of users around the world. The main goal of implementing decentralization is to ensure security. Due to the dispersion and duplication of data in the network that ensures the functioning of the cryptocurrency, it is difficult to "knock down" by organizing an attack.
To achieve decentralization there is a need for Proof-of-Work, Proof-of-Stake or its combinations. These algorithms are required for reaching consensus in the blockchain. They are used to confirm transactions and create new blocks. In this article you can read more about PoW, PoS, their differences and ability to protect distributed systems from DoS attacks, spam mailings, and etc.
In the case of PoW, it is necessary to understand the importance of computational power and hash rate. Sometimes it happens that there is very large computational power for mining that appears to be in one person's (group’s) hands and because of that the risk of centralization of cryptocurrencies increases. This is a negative phenomenon since concentration increases the vulnerability of the system as a whole. Owning more than half of the computing resources, theoretically, you can make the cryptocurrency work according to your scenario. That is, you can submit incorrect data to the network and it will accept this data as true information, since the truth will be confirmed by most of the computing resources. But speaking not only about the theory, there are also real cases of such actions and it is called the 51 percent attack (51% attack). The 51% attack is considered to be one of the most serious threats for many cryptocurrencies. If one miner or a group of them have more than 51% of the computing power in their hands, then it is possible to gain partial control over the network with a PoW algorithm. In the case of PoS, a person (a group of people) has to gather 51 percent of crypto (the stake) to carry out a 51% attack. Although, some people believe that here the risk is not always worth taking, because the attacker will eventually lose money in this situation.
If an attacker successfully carries out an attack, they can selectively block transactions, undo transactions that have already taken place, or even reorganize the blockchain. As a result, it is possible to rewrite previously confirmed blocks and even divide the network into several chains.
Having 51% of the power hackers:
- don’t give other miners the opportunity to find blocks;
- double-spend coins to steal from service providers, stock exchanges and instant exchanges;
- fork the main blockchain, splitting the network into two competing chains;
- don’t let transactions or blocks to be confirmed;
- collect all block rewards and transaction fees during the attack.
Did you ever think about the cost of the 51% attack? Researchers published their work on this topic and here what they’ve discovered:
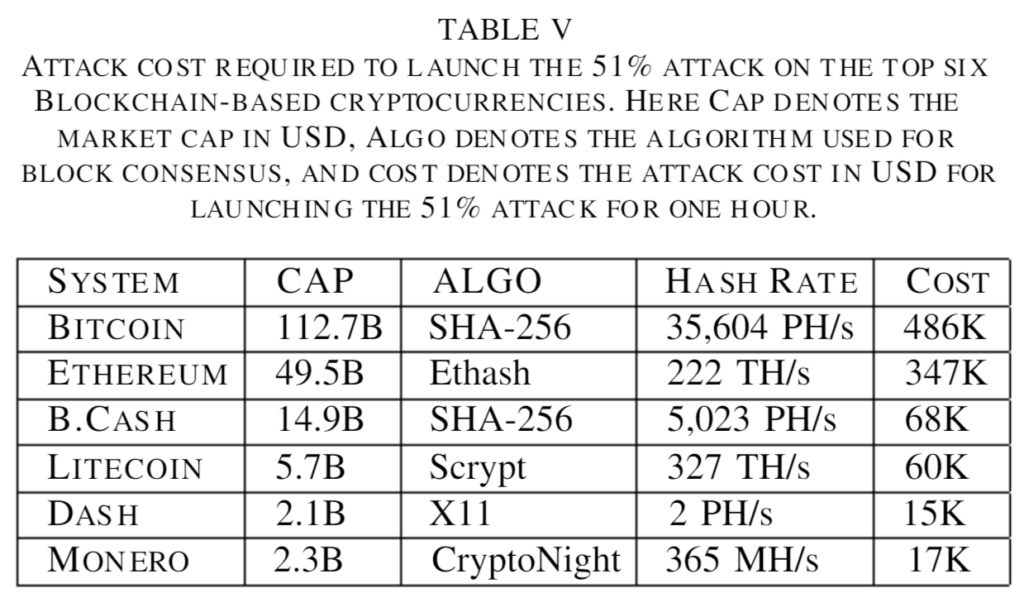
Data received in April 2019. As you can see, to attack Bitcoin, you need to spend $486,000 per hour. And it costs only $15,000 per hour to attack Dash (with a market cap of $2.1 billion). Ethereum 51% attack costs $347,000 per hour.
51% attacks in crypto history
Earlier it was said about real cases of 51% attacks which have already happened. Let’s see some examples:
- Year 2018 has been eventful for 51 percent attacks. Just look at it: major exchanges lost in Zencash (ZEN) about $500,000, in Verge (XVG) - $1.7 million and $90,000 in Monacoin.
- Also in 2018, Bitcoin Gold (BTG) altcoin network went under the 51% attack providing predators with the ability to take $18 million from large exchanges like Bitfinex, Binance and others.
- Through a series of double spendings a squad of hackers have hacked into the Krypton and Shift blockchain projects. It happened in 2016 and cost the project about 20,000 tokens.
- Aurum Coin got the 51% attack. Above $500,000 were stolen from the exchange called Cryptopia.
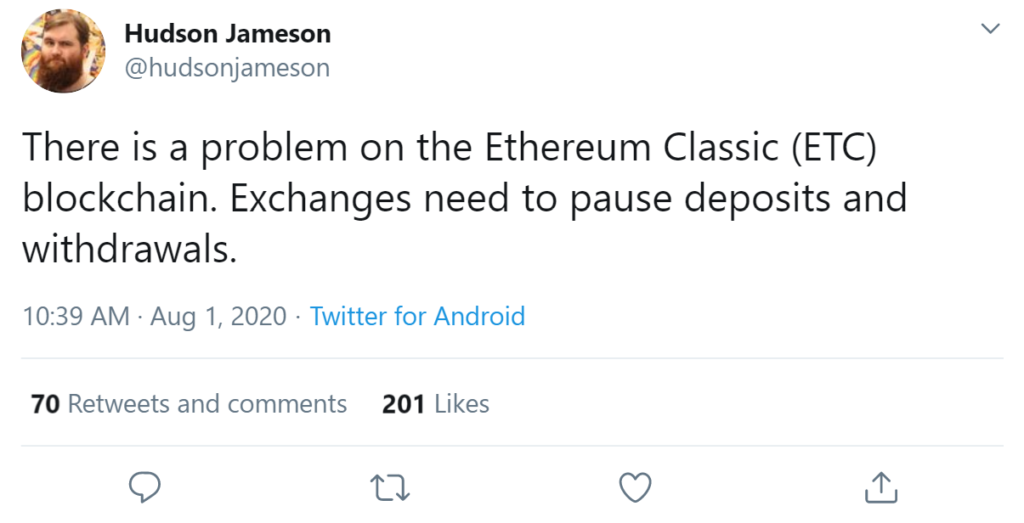
- There was a recent 51% attack on Ethereum Classic. It happened on August 1st, 2020. The network was split and 3,693 "extra" blocks were added to it. One of the first persons who noticed this was Jameson Hudson (a researcher), he posted a tweet:
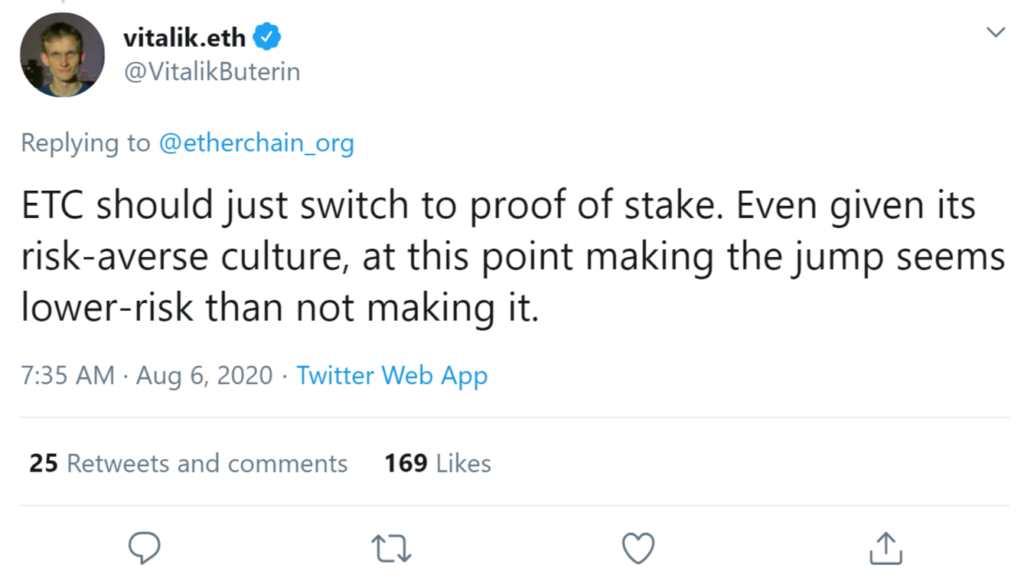
In addition to this, on August 6th, 2020, the Etherchain service discovered that another 51% attack occurred on the network. This time more than 4,000 extra blocks were mined. And here’s what Vitalik Buterin thinks about it:
Looking back, we can see that at the beginning of 2019, the Ethereum Classic network was already undergoing a 51% attack.
It is clear that nobody is immune to 51% attack but every network puts its best leg foremost to avoid it. Different networks think of different ways to protect themselves from this attack. For example, as said above, Vitalik Buterin found a theoretical way to avoid it. He offered to add independent nodes to the system to monitor the consensus, increasing the stability of the network to almost 100%. That is, for a successful attack on the network, an attacker will need to control 99% of the blockchain nodes instead of 51%. However, the method has not yet been applied. Also, Buterin recommended moving the blockchain from PoW to PoS. As in PoS blocks are being created not via owning the computational power but by owning the cryptocurrency itself.Another method is to increase the amount of confirmations. As with ZClassic (ZCL): they increased the amount of confirmations for all deposits to 200 or even 500 times. Although, that is not very convenient for users as the transaction time takes up to several days. Another example is the Komodo (KMD) solution. They offered a one-stop solution. It is suitable for all cryptocurrencies with a small hash rate, both for PoW and PoS algorithms. The basic idea to prevent the 51% attack is to permanently record the state of the coin's blockchain on the Bitcoin blockchain. It is extremely difficult to attack the BTC blockchain, and this is exactly what the KMD developers offer to use.
Listed above cryptocurrencies are just examples of the 51% attack, they are not worse or better to invest in. This article has no financial advice and it’s always at your discretion what decisions on investment to make.

